Threats delivered over encrypted channels continue to rise

Encryption is the default for online communication, with nearly all web traffic protected by secure protocols like TLS/SSL. Yet, as encryption becomes more ubiquitous by the day, so do the opportunities for threat actors to exploit encrypted channels.
The same encryption that safeguards legitimate activities also acts as a conduit for malicious ones. Attackers are using encrypted channels to bypass traditional defenses, concealing malware, phishing campaigns, cryptomining/cryptojacking, and data theft within encrypted traffic.
The Zscaler ThreatLabz 2024 Encrypted Attacks Report examines this evolving threat landscape, based on a comprehensive analysis of billions of threats delivered over HTTPS and blocked by the Zscaler cloud. The report highlights the more recent trends, top threat categories, most common targets of encrypted attacks, and other insights into how attackers are weaponizing encrypted traffic.
5 key findings on encrypted attacks
The ThreatLabz research team analyzed 32.1 billion encrypted attacks blocked by the Zscaler cloud between October 2023 and September 2024 to identify and understand the latest threat patterns. The following subset of findings highlights some of the most prominent trends and targets.
1. Steady growth in encrypted attacks: The Zscaler cloud blocked an unprecedented volume of attacks embedded in TLS/SSL traffic during the analysis period. Encrypted threats accounted for 87.2% of all blocked attacks, representing a 10.3% year-over-year increase in encrypted attacks and reflecting the growing reliance on encryption by threat actors to hide their malicious activities.
2. Malware dominates the landscape: Malware remains the most prevalent encrypted threat, representing 86.5% of blocked attacks. This trend highlights the adaptation of malware tactics to thrive in encrypted channels, using encryption to mask payloads and evade traditional security and detection measures.
Zscaler
Figure 1: Top threat categories observed
3. Cryptomining/cryptojacking, cross-site scripting, and phishing threats surge: Cryptomining/cryptojacking and cross-site scripting (XSS) are among the fastest-growing encrypted threats, with year-over-year increases of 122.9% and 110.2%, respectively, while phishing saw a notable 34.1% jump. It’s possible that these spikes were fueled by the growing use of generative AI technologies, which make it easier to create advanced cryptomining scripts, automate malicious XSS scripts, and execute highly convincing phishing campaigns.
4. Manufacturing tops list of most impacted industries: The manufacturing, technology, and services industries were the most targeted, with manufacturing enduring 13.5 billion encrypted attack attempts between October 2023 and September 2024.
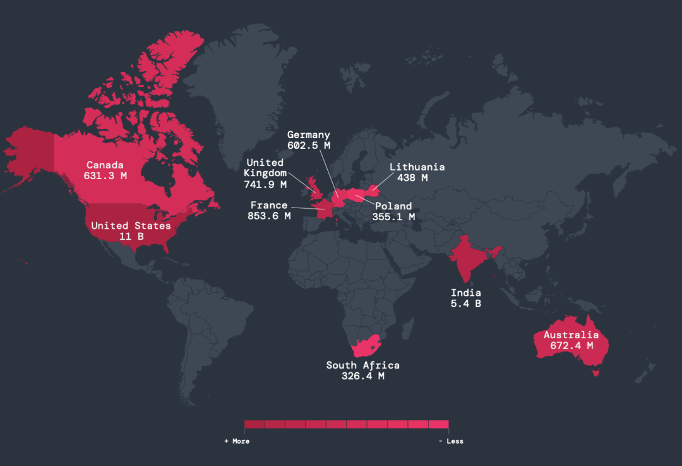
5. The US and India remain top targets: Receiving 11 billion (US) and 5.4 billion (India) encrypted attacks during the ThreatLabz analysis period, the US and India retained their positions as the most targeted countries, followed by France, the United Kingdom, and Australia.
Zscaler
Figure 2: A map of the countries that experience the most encrypted attacks
Evolving encrypted attack trends
ThreatLabz uncovered many significant evolving trends in encrypted attacks, from attackers leveraging encryption channels to siphon off sensitive data to adversary-in-the-middle (AiTM) methods using advanced tools and TLS/SSL encryption to create nearly undetectable phishing campaigns. The report offers examples of each.
One notable trend explored in detail by ThreatLabz is the growing abuse of cloud services by advanced persistent threat (APT) groups. By blending in with legitimate cloud services traffic, APT groups can take advantage of the default use of TLS/SSL encryption enabled to help them evade network security controls. ThreatLabz delves into this trend, providing a detailed analysis that includes:
- Top APT groups abusing cloud services
- Top 10 cloud services abused
- Top services abused for payload delivery
- Most common tactics used in cloud service abuse
How Zscaler stops encrypted threats
The Zscaler Zero Trust Exchange provides a powerful solution to stopping encrypted threats, starting with eliminating blind spots via its TLS/SSL inspection capabilities and AI-driven defenses. Here’s how Zscaler tackles encrypted threats at every stage of an attack.
Minimize the attack surface: Unchecked encrypted connections, such as those through VPNs or exposed workloads, can expand the attack surface and allow attackers to hide in plain sight. Zscaler eliminates this risk and the attack surface by keeping applications and services invisible to the internet. This approach stops encrypted threats from reaching critical applications and systems, providing proactive protection that doesn’t rely on shared network access.
Prevent initial compromise Zscaler Internet Access™ (ZIA) performs full TLS/SSL inspection to verify every connection and stop hidden threats without sacrificing performance. ZIA’s inspection capabilities leverage AI-powered analysis and inline detection to quickly identify and block sophisticated threats within encrypted traffic. This approach eliminates the need for traditional, resource-intensive physical appliances, allowing organizations to handle encrypted traffic growth easily and without disruption.
Eliminate lateral movement: Attackers often aim to move laterally within networks once they gain entry. Zscaler prevents this with zero trust segmentation and AI-powered, context-aware policies delivered through Zscaler Private Access™ (ZPA). ZPA enforces granular access controls, limiting users to specific applications based on identity, context, and policy. This replaces complex rule-based network segmentation with streamlined, identity-based access control. Additionally, Zscaler uses deception technology, setting decoys to detect and thwart lateral movement attempts within encrypted traffic.
Block command-and-control callbacks Malware often relies on encrypted channels to communicate with C2 servers, enabling attackers to execute commands, download additional malware, or exfiltrate sensitive data. ZIA inspects outgoing (northbound) and incoming (southbound) encrypted traffic to disrupt C2 communications. Zscaler’s AI-powered data loss prevention tools detect and block malicious traffic, preventing sensitive data from being exfiltrated and encrypted C2 callbacks from compromising the network.
Case study: Learn how Wipro blocked 8.2M encrypted threats in one quarter with Zscaler
By replacing traditional firewalls and VPNs with Zscaler, Wipro strengthened its defenses with inline TLS/SSL inspection of all internet and SaaS traffic to detect and block encrypted threats. Read their story here.
Why comprehensive TLS/SSL inspection matters
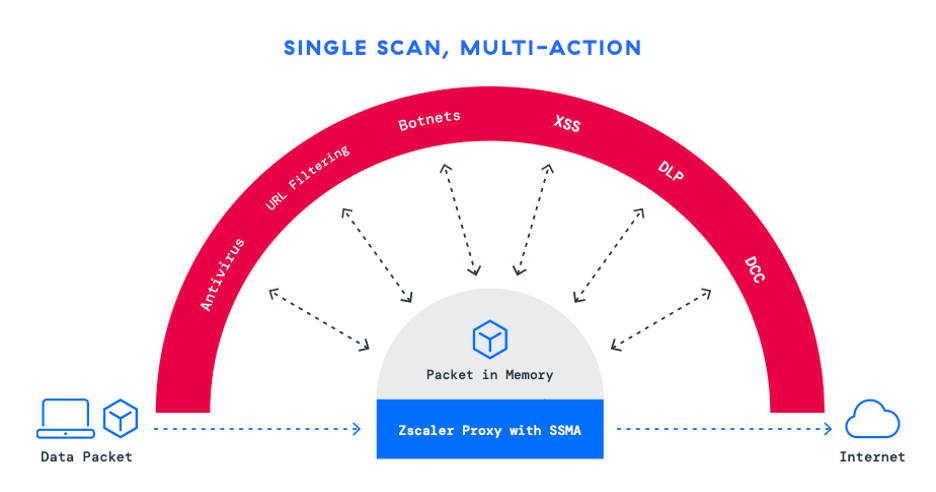
The foundation of Zscaler’s defense against encrypted threats is its full TLS/SSL inspection capabilities, enabled by a scalable proxy-based architecture. Unlike traditional hardware-based solutions that force organizations to compromise between security and speed, Zscaler’s cloud-native approach allows organizations to fully inspect traffic at scale with its Single Scan, Multi-Action engine—a unique feature that processes traffic once to apply multiple security controls simultaneously. This helps organizations to:
- Inspect 100% of encrypted traffic: Unlike solutions that inspect only a fraction of encrypted traffic due to hardware constraints, Zscaler’s cloud-native architecture ensures every packet is inspected without exception.
- Layer advanced security controls: Inline, AI-powered security controls detect and block threats embedded in encrypted traffic.
- Maintain high performance: Zscaler’s architecture eliminates bottlenecks typically associated with hardware appliances.
Zscaler
Stay ahead of encrypted threats
The findings in the ThreatLabz 2024 Encrypted Attacks Report make it clear that threat actors are consistently evolving with the help of encryption and AI technologies to evade detection and maximize their impact.
Dive deeper into the latest research and learn more about how to stay ahead of encrypted threats. The full report offers:
- In-depth analysis: Detailed findings and case studies on how attackers are leveraging encryption.
- 2025 predictions: Expert insights into where the encrypted threat landscape is headed.
- Actionable best practices: A practical checklist for improving your defenses against encrypted attacks.
Protect your organization from encrypted threats. Get your copy of the report today.

